How to identify threats, plug security gaps and proactively avoid the next shutdown for oil and gas, power plants and other industrial facilities
As the lines blur between the digital and real worlds, cyber-physical attacks are proliferating. One of the first "cyber-physical weapons", Stuxnet was discovered to target industrial control systems (ICS) in 2010. Since then, there has been attacks on other oil and gas (Triton), power and energy (Crashoverride/Industroyer), and water (the recent attack in Oldsmar, Florida) facilities.
Cyber-physical attacks have major consequences for human safety. A compromised controller in a refinery or manufacturing plant can result in a localised explosion or contaminated batch processing. Attacks on Information Technology (IT) systems also translate into devastating outcomes. Case in point: the ransomware attacks on University Hospital Düsseldorf in 2020 and on the Colonial Pipeline in 2021 culminated in the loss of a patient’s life and the shortage of gas supply respectively.

Business owners often do not know how to respond to attacks or even how to begin safeguarding their cyber-physical systems. With limited resources, cyber-physical aspects might not be top of mind for them. In this article, we will discuss the key risks in the cyber-physical security ecosystem and outline a few strategies to help businesses prevent and minimise damage from such attacks.
Supply chains and humans pose major risks for cybersecurity
Threat actors can be broadly classified as insiders, script kiddies, hacktivists, cyber criminals, and nation state actors, each of whom have their objectives and modus operandi.
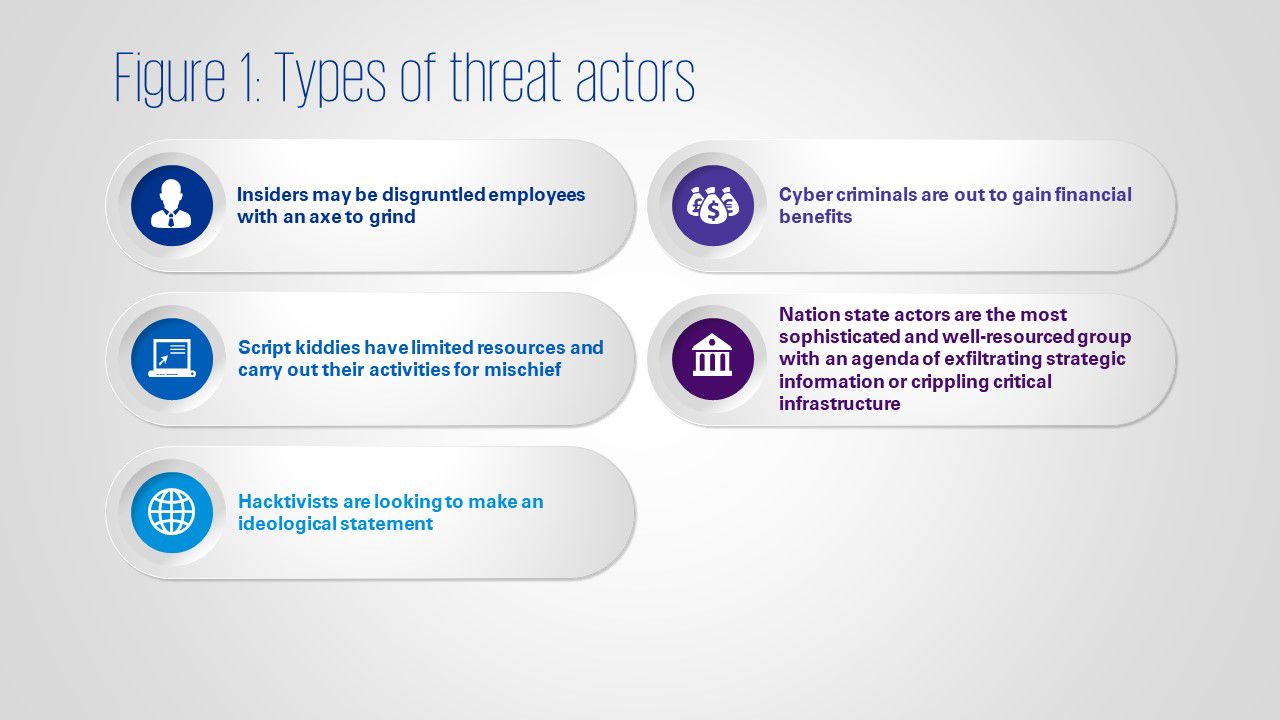
Internationally, there is a weak definition as to which types of cyber-attacks are considered ‘war’. This allows states to push the boundaries in the types of cyber-physical attacks they launch and how they do so. As such, nation state actors arguably pose the greatest present danger, given their access to resources.
Launching state-sponsored attacks often take years to prepare for but can be used to gain a strategic advantage in geopolitical clashes. Attacking critical infrastructure like water plants, for example, may contaminate a nation’s water supply; attacking electrical grids may lead to outages, which cause cascading impact to downstream systems that depend on power supply.
Supply chains have also surfaced as a major risk recently - broadly categorised into hardware supply chain risks, software supply chain risks and service provider supply chain risks. For example, installing backdoors into embedded systems can disrupt hardware supply chains, while injecting malicious codes into updates can compromise software supply chains such as in the SolarWinds incident. Service provider supply chains can also be compromised by contractors with corrupted devices that connect into the ICS.
The weakest link in the cybersecurity chain are humans. Even with industry-leading processes and technologies in place, unaware, untrained, or unconcerned employees are risks. Their lack of vigilance can open doors for threat actors to inflict damage on ICS.
Therefore, well-practiced business continuity plans (BCP) and disaster recovery plans (DRP) are key to a safe and quick recovery. These plans need to be continuously updated and well-communicated among all stakeholders within the ICS. They can come in the form of playbooks that are regularly rehearsed during emergency exercises involving senior management, operators and first responders.
The following are some strategies we recommend:
Proactively prevent the next shutdown with network segmentation and security monitoring
1. Network segmentation
There is merit in designing an ICS resilient to cyber-physical attacks. It involves segmentation of the network into zones and conduits. This is the premise of IEC 62443, a series of standards to guide on secure ICS. It covers general guidance, policy and procedures, system technology and design, as well as component requirements.
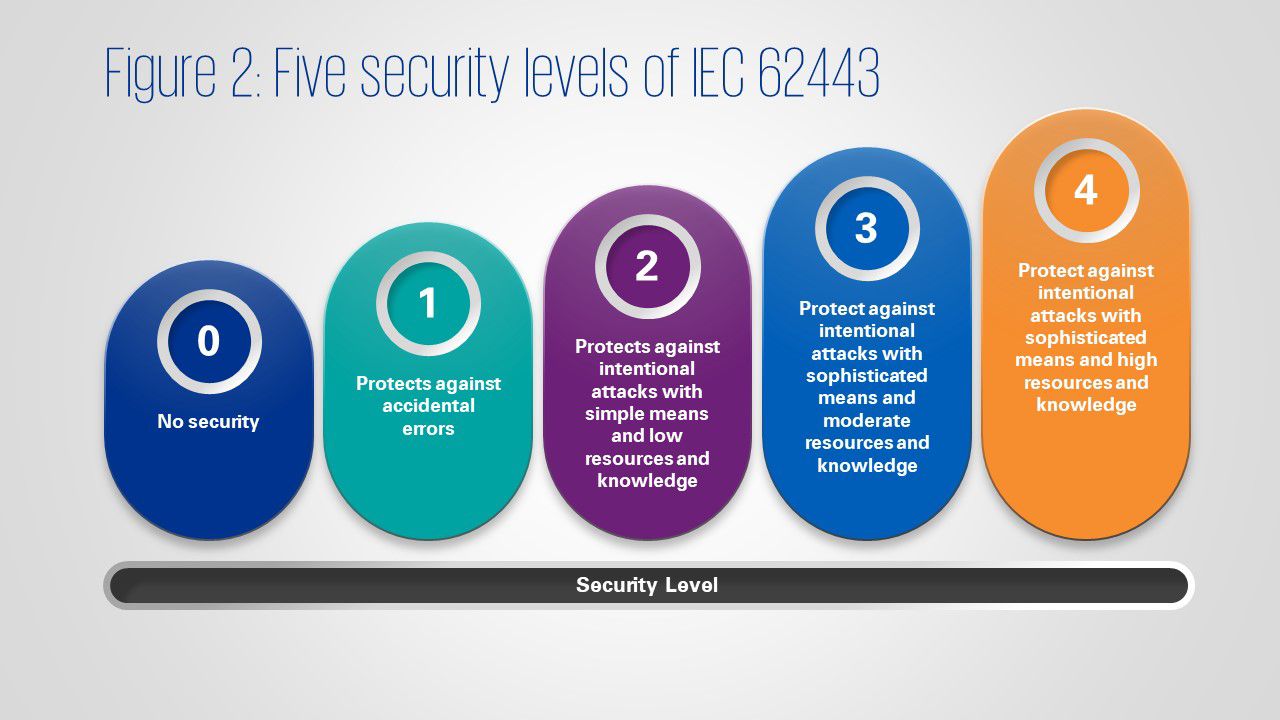
IEC 62443 defines five Security Levels (SL) – see figure 2.
SL 0 for safety-related systems is not acceptable. For safety systems, the requirements of SL 1 should be the baseline.
2. Cyber Process Hazard Analysis
Once the ICS has been properly designed, a Cyber Process Hazard Analysis (C-PHA) can be conducted – see figure 3. The Cyber Hazard and Operability (CHAZOP) method is commonly used. This involves dividing the entire process into sections. Each section has its distinct function that results in a property or characteristic change in the process feed. For example, the start to end of a pressure compression stage may be taken as a single section; or the start to end of a fire heater stage may be taken as another section.
After sections are identified, the team assesses whether a pre-determined scenario based on guide words can occur and if so, how. For process safety, guide words may include “high/low/reverse flow”, “high/low pressure”, “high/low temperature”. In cybersecurity context, guide words can be based on the STRIDE model – spoofing, tampering, repudiation, information disclosure, denial of service, elevation of privilege. Each scenario is tabulated and given a risk score. Control measures to mitigate the likelihood or impact of a cyber-physical attack are also recommended. This exercise is repeated for each section.
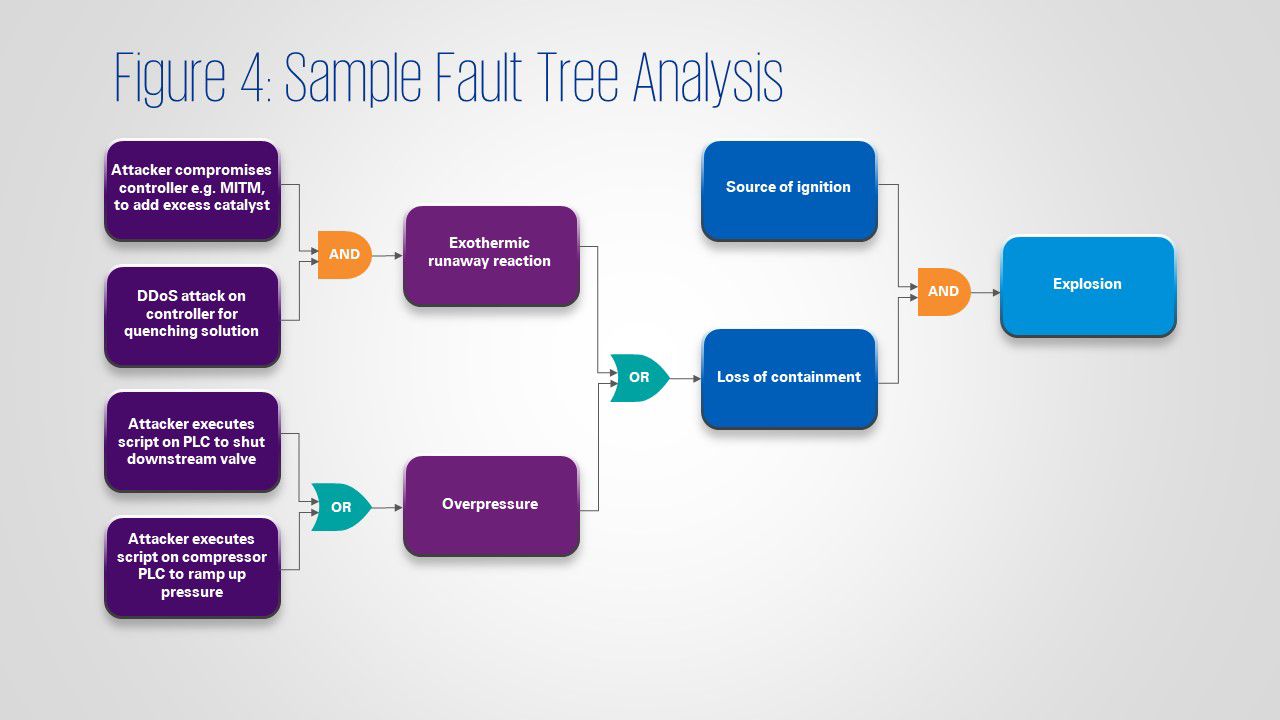
3. Fault Tree Analysis
CHAZOP is not the only method to conduct C-PHA. A more graphical approach is the Fault Tree Analysis (FTA) – see figure 4. FTA consists of a series of events with logical gates e.g. AND, OR, NOT. With consecutive events allowed to happen, an eventual occurrence results in, for example, loss of confinement and explosion.
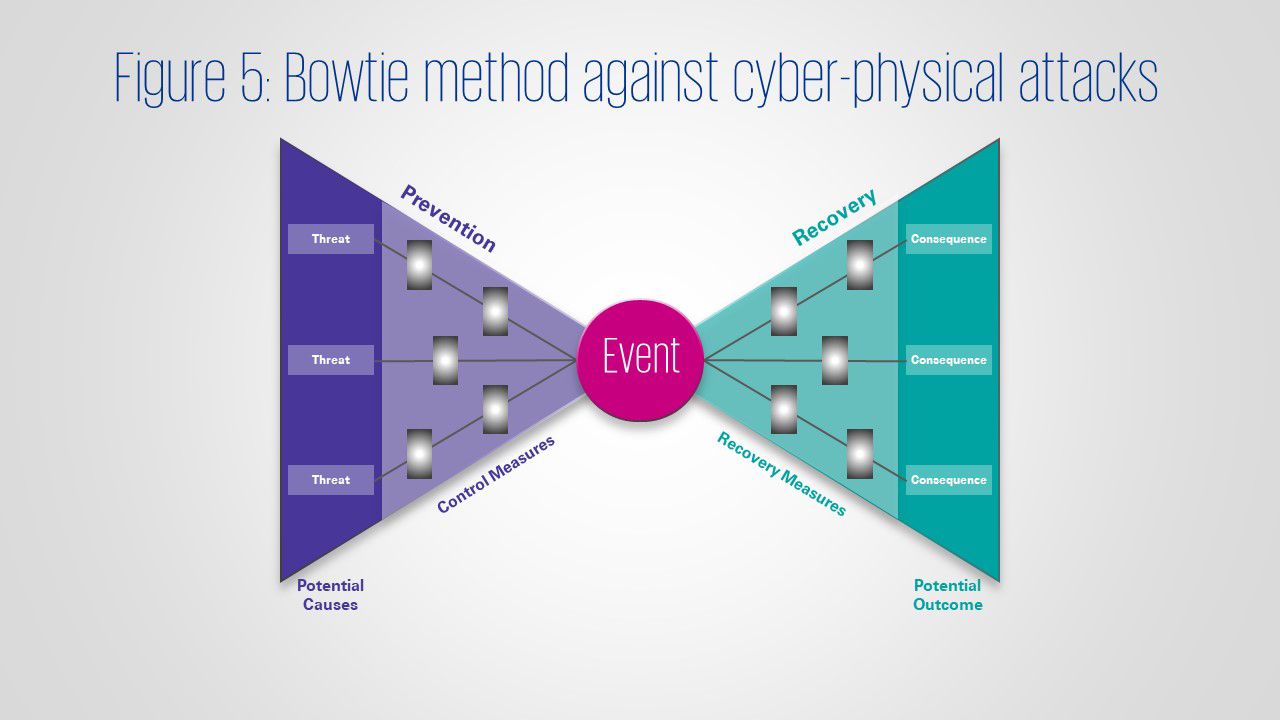
4. The Bowtie method
Another method called Bowtie – see figure 5, is based on the Swiss Cheese model of accident causation used in risk analysis and management. The Bowtie method aims to prevent cyber-physical attacks by putting in place barriers that prevent a threat source from causing an event. It also prevents or reduces negative impact by creating post-event barriers.
5. Network security monitoring
To detect cyber-physical attacks, ICS owners must implement both Network Security Monitoring (NSM) and process anomaly detection. Both are complementary.
NSM is achieved by implementing solutions to dissect and analyse network traffic, as well as to issue alerts when rules are violated. However, NSM can only go as far as there are packets to monitor.
At field device level, i.e. Level 0 of the Purdue Model1, communication is mainly via digital +/- 24VDC or analog 4 to 20mA signals, ICS owners must depend on process anomaly detection to pick up aberrations. This involves checking that process sensor readings are normal. Process rules include out of band limiting, where alerts are triggered when process variables exceed upper and lower bounds, for example, when vessel pressure exceeds maximum safe operating pressure; and rate of change control, where alerts are triggered when process variables rise or fall too fast. Artificial intelligence and machine learning are also increasingly being used to correlate logs to enhance advanced threat protection.
Avoiding disruption of services via ‘graceful degradation’
A crucial aspect in minimising the impact of a cyber-physical attack on ICS is ‘graceful degradation’, or the practice of failing a process safely to ensure that the inherent function of the system remains despite a portion of it being rendered inoperative.
The difference between an elevator and an escalator provides a fitting analogy for graceful degradation. An escalator still allows people to walk from one floor to another even if it has stopped working, and is an example of how graceful degradation can be designed. In contrast, if an elevator is not working, people will not be able to move between floors.
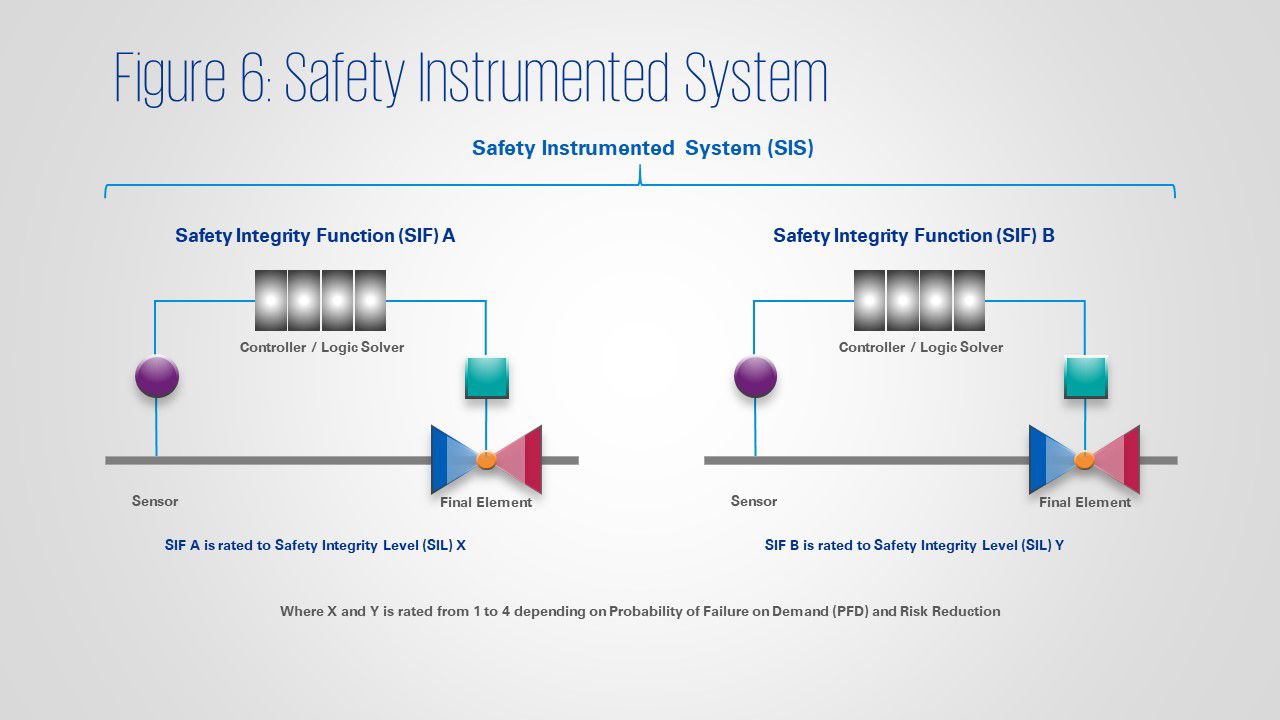
The safest engineering method to shut down an ICS process is to implement Safety Instrumented Systems (SIS). Under the International Electrotechnical Commission (IEC) Standard 61511 - Functional Safety: Safety Instrumented Systems for the Process Industry Sector, an SIS must meet the desired Safety Integrity Level (SIL) for a Safety Instrumented Function (SIF). For example, if an SIS consists of a SIF to shut off the process when pipeline pressure exceeds a certain threshold, a SIL 2 rating would ensure Probability of Failure on Demand (PFD) of 0.01 to 0.001. SIL 2 is commonly required in chemical process plants. An SIS should either be physically or logically separated from the Basic Process Control System (BPCS) to prevent a Triton-like attack, where the attackers landed on the Triconex SIS controller, shutting down the process.
Besides bringing the ICS to a safe state, graceful degradation considers maintaining availability. Processes can be designed with redundancies and manual overrides. For example, if one line is interrupted, a bypass can be manually opened to allow flow to continue. Alternatively, if a Distributed Control System (DCS) is compromised, operators can start up the compressor locally. Unfortunately, the push for automation has led to many operators lacking skills to run equipment manually. This training needs to be looked into.
How can KPMG help you?
As cyber-physical threats become a reality, KPMG in Singapore consistently delivers high-quality results through a combination of technological expertise, deep business knowledge, serviced by creative professionals passionate about protecting and growing your business. Our Operational Technology (OT) team comprises industry professionals trained in both cyber security and engineering, with proven track records in designing, building, operating, and maintaining critical ICS. Supporting them are more than 500 cyber professionals in Asia Pacific and resources in 147 countries globally.
Drawing on experience from across the cyber security continuum — cyber strategy and governance, cyber transformation, cyber defense, and cyber response — we apply leading security practices, as well as develop new ones fit for purpose.
Among our service offerings are: cyber maturity assessments, risk assessments, threat modelling, vulnerability assessments, penetration testing, compliance audits, threat hunting, red or purple teaming, cyber security exercises, incident response and training.
The firm has also won numerous awards for our cybersecurity work, such as The Peak Laureates 2020 and Leader of Forrester WaveTM 2019. Critical information infrastructure owners count among a good number of our clients.
No matter where you are on your cyber security journey, we bring the expertise to help you reach your destination.
1The Purdue model is a network segmentation-based reference architecture for ICS security.
